In a world where cyber threats are constantly evolving, traditional perimeter-based security is no longer enough. Small and medium-sized businesses (SMBs) are increasingly becoming targets for attackers—not because they’re less important, but because they’re often less prepared. This is where Zero Trust Security comes in.
What is Zero Trust?
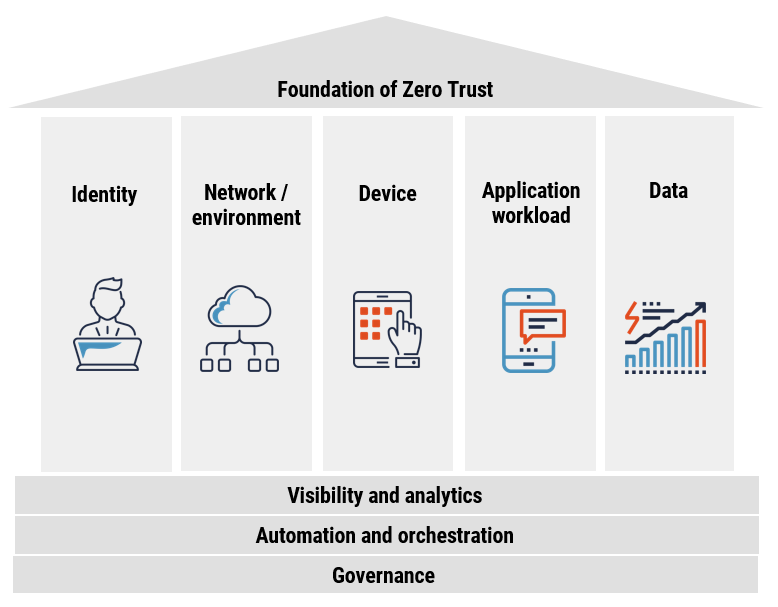
Zero Trust is a security model based on a simple premise: trust no one, verify everything.
Rather than assuming that users and devices inside a network are safe, Zero Trust continuously verifies all access requests, regardless of origin. It’s a shift from the outdated “castle and moat” approach—where everything inside the network was trusted—to one that assumes breach and actively works to prevent it.
Why SMBs Should Care
You don’t need to be a large enterprise to benefit from Zero Trust. In fact, SMBs are ideal candidates for Zero Trust because:
- They often have flat networks with fewer security layers
- They may rely heavily on cloud services and remote access
- They usually lack dedicated cybersecurity teams
Implementing a Zero Trust framework can dramatically reduce the risk of data breaches, ransomware infections, and insider threats.
Core Principles of Zero Trust
Zero Trust isn’t a product—it’s a framework. Here are its foundational principles:
1. Verify Explicitly
Always authenticate and authorise based on all available data points: user identity, device health, location, and workload.
2. Use Least Privilege Access
Grant users only the minimum access needed to do their job. Role-based access controls (RBAC) and just-in-time (JIT) permissions are key here.
3. Assume Breach
Design your system with the expectation that attackers are already inside. Segment your network, monitor access, and respond quickly.
Best Practices for SMBs
Implementing Zero Trust doesn’t have to be overwhelming. Here are practical steps SMBs can take:
- Adopt Multi-Factor Authentication (MFA)
Enforce MFA across all critical systems—especially email, cloud services, and VPNs. - Map Your Digital Environment
Understand what assets, applications, and users you have. You can’t secure what you don’t know exists. - Segment Your Network
Use VLANs, firewalls, or software-defined networking to separate sensitive data from general access. - Monitor Device Compliance
Use tools like Microsoft Intune or endpoint detection and response (EDR) platforms to ensure only secure, updated devices can connect. - Limit Access with Conditional Policies
Implement policies that restrict access based on device type, location, time, or risk level. - Log, Monitor, and Respond
Enable detailed logging and review access patterns regularly. Use SIEM solutions (like Microsoft Sentinel) to detect anomalies early.
Common Challenges (And How to Overcome Them)
| Challenge | Solution |
|---|---|
| Limited IT resources | Use managed services or MSPs for setup and support |
| Legacy systems that can’t adapt | Isolate them with strict segmentation and monitoring |
| Staff resistance to change | Educate and train users on the “why” behind Zero Trust |
Final Thoughts
Zero Trust isn’t a switch you flip—it’s a journey. But for SMBs looking to future-proof their security posture without breaking the bank, it’s one of the most effective strategies available today.
At FYDUS IT Solutions, we help businesses implement practical, scalable security models like Zero Trust. Whether you’re just starting out or looking to enhance your existing defences, we can guide you every step of the way.